Today we want to introduce you to an analysis technique that will improve defense planning by more accurate prioritization of threats. This technique integrates different types of information based on a particular threat conception. This conception deviates from the actor-centric definition which is popular in the industry. Therefore, in this chapter, we will try to describe these differences.
Threats are properties if the terrain
Threat — A method (techniques or tactics) an attacker (actor, agent, adversary) can possibly use to achieve or advance towards a particular goal. Threats are inherent in any terrain (IT infra, software, process) regardless of the attacker’s capabilities or intent, and are not necessarily caused by a weakness (software flaw or vulnerability).
For instance, an organization that serves web applications must be concerned about web attacks. An organization that uses credentials should be concerned about credential attacks. If an organization doesn’t have the means to manage their credentials at scale, the threat (of credential attacks) is greater for them.
What you own dictates how an attacker can approach you. If you don’t use the cloud, an attacker can’t use cloud techniques on you, no matter how willing or capable he is. If all your employees use Macs, malware threats are much less of a concern for you. To better understand the threats, we must know our terrain better and look at it through the lenses of the adversary.
This is possible with scenario planning exercises that are focused on our core assets. These are essentially brainstorming sessions aimed at listing every possible way an adversary could attack (or abuse) the system in question. The resulting list contains hypothetical threat scenarios that can then be prioritized and counteracted. So these scenarios don’t need to be probable, but only possible. Similarly, we are not interested in discovering weaknesses at this stage.
Once the threats are known, then counteracting is a matter of organizing your terrain. With the knowledge of prioritized threats (threat landscape, threat map or threat library) we can better direct our strategic and operational efforts towards mitigating them.
This type of threat analysis contrasts with the actor-centric method favored in the industry. I argue that the actor-centric analysis is flawed for two reasons:
-
- Actor-centric analysis considers threats as a property of the adversary. But adversaries can be highly adaptive. Therefore, focusing efforts on countering an adversary’s current capabilities is essentially hoping that they won’t adapt (or, as some argue, forcing them to). Since it is not possible to know whether or how an adversary will adapt, your preparation can’t go beyond what is current.
- Actor-centric analysis tries to observe what’s happening outside (by analyzing the threat actors) and apply these insights to cyber defense. However, the relevance of these insights becomes an issue. Currently, the industry is trying to overcome this by categorizing threats by geography and industry. But this type of correlation is not always useful. Also, “What did happen? /What did we find?” offers a very narrow window compared to“what is possible to happen?”.
Whereas, if threats are considered to be a property of the terrain, it becomes possible to know and plan for every possible threat in advance (assuming you have knowledge of your terrain). Afterwards, you can prioritize threats by using actor-centric (and possibly other) insights and then start implementing controls to mitigate them. Where controls are insufficient or absent, there is a gap that an adversary can take advantage of. Gaps make it more likely to introduce weaknesses, and weaknesses can be exploited to actualize threats.
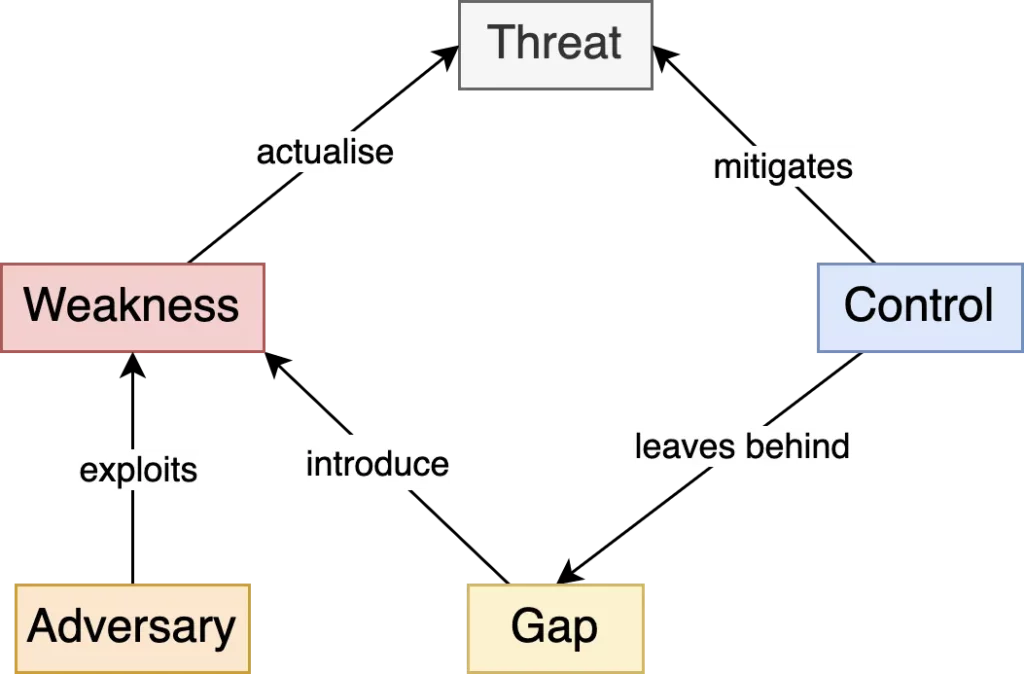
As discussed above, we consider threats to be a property of the terrain, independent from an actor’s intent and capabilities. Terrain dictates the battle. Similarly in cyber intrusions, what you own (assets, personnel, processes etc.) dictates how an adversary can possibly approach you. Therefore, threats are the methods & techniques an adversary may use to achieve their objective (whatever that is). To be able to assess threats, one should first have sufficient knowledge of his terrain. That means the most crucial groundwork to be done is scenario planning. (see: chapter 1)
Stemming from this thought, four data points are the most useful on deciding which threats are most relevant and should be prioritise. These are:
-
- Posture risk
- Incident post-mortems
- Vulnerabilities
- Threat intelligence
Now we shall elaborate each one.
1. Posture Risk
Security posture represents how effectively we can mitigate a threat with our existing controls. Not all security controls can mitigate all of the threats. For instance, we can not expect a WAF to counter endpoint-related threats (e.g: malware). Another thing to note is that almost all security controls can be bypassed. Therefore, there will always be a residual risk.
To use this data point, we should gather all the threats we have listed during our scenario planning sessions, and assess whether our controls are sufficiently mitigating each threat. You may group similar threat scenarios under categories to make things easier. An example could be like the following:
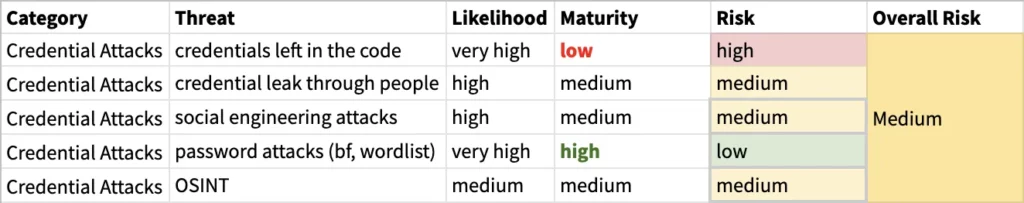
If the controls are not sufficient to mitigate a threat, or there are no controls whatsoever, then this called a weakness. Although sounding similar, a weakness is not the same with a vulnerability. A vulnerability is what an adversary can exploit to materialise threats. A weakness on the other hand, is what’s causing the system to introduce these vulnerabilities. For example, if you’re not scanning your codebase for hardcoded credentials, these credentials will be introduced to your codebase much more often. Lack of the control (source code scanner) is a weakness, whereas the hardcoded credential itself is the vulnerability, which the adversary will exploit.
2. Incident post-mortems
An incident represents an actualised threat. Therefore, they are the most important data points for our analysis. All incidents, especially the ones where adversary has reached its objective, should be thoroughly examined to uncover all the TTPs. After that, these TTPs should be mapped to our threat library to see which of the threat scenarios we listed has materialised. Post-mortems are also useful for unrevealing the weaknesses (a.k.a posture gaps), which is causing the vulnerabilities to be introduced to the system.
3. Vulnerabilities
Vulnerabilities are the opportunities an adversary may abuse to enter our systems and achieve their objectives. Their existence do not pose active threats on their own. But if the system is producing same kind of vulnerabilities very often, it usually points to a gap in our posture (weakness) and will more likely be discovered by an adversary. These should be noted and included in our threat assessment.
4. Threat Intelligence
Threat intelligence can provide useful insights into adversary intent, drivers and their TTPs. Intent and drivers can be used to understand the type of actors that are likely to target our systems. And TTPs can be mapped to our threat library to indicate which scenarios are more likely to actualise.
Using these four data points, it will be possible to assess which threat scenarios are more likely to materialise (and some have already). This will give us a good prediction window, where we can focus our efforts and better prepared for the cyber threats.


