Analysis of APT37 New Year Attacks
Analysis of APT37 New Year Attacks

Summary
This is the analysis report of a sample which is tied to a campaign conducted against South Korean Unification Ministry – 1 January 2019. We have identified that the aforementioned malware possesses information collection capabilities. We also suspect that the malware possesses remote command execution capabilities. Anti analysis techniques are employed. Considering this information, we are confident that the implant functions as a spyware. Although having several distinctive features, the tradecraft of this implant is similar to those from “Operation Kimsuky”.
General Information
| Name (UTF-8) | Type | MD5 |
| ¦¤Ãª ¢+-Ô¬_.exe (Main Sample) | PE32 executable (GUI) Intel 80386 | e9c1dec196441577816d85dc304d702d |
| Resources/SRV/129(HncChecker.dll) | PE32 executable (DLL) (GUI) x86-64 | 8058beb593166f1cc16d6cd3f6784577 |
| Resources/SRV/130 (HncChecker.dll) | PE32 executable (DLL) (GUI) Intel 80386 | a65b5e6f104d01916feadd180c8161c2 |
| Resources/SRV/131(190101-½Å³â»ç_Æò°¡.hwp) | Hangul (Korean) Word Processor File 5.x | 07fba69097eff4f0773cff8414f72a80 |
File Sections
| NAME | VSIZE | RSIZE | ENTROPY | MD5 |
| .TEXT | 32752 | 32768 | 6.61 | 9e1834cb74f3a3d2112b89886d57a298 |
| .RDATA | 14328 | 14336 | 5.91 | 8d19678981eac0f477f873dda1a86877 |
| .DATA | 14784 | 5120 | 3.21 | 564d9be0c62a0ea837e794ffb8ddedb8 |
| .DATA0 | 340032 | 340480 | 7.95 | 95b124da70660628261879c6ee701224 |
| .TLS | 24 | 512 | 0 | bf619eac0cdf3f68d496ea9344137e8b |
| .DATA1 | 76576 | 76800 | 7.62 | 6c8ff14aea5d965d3dd9a5bbb9a07512 |
| .RELOC | 3568 | 3584 | 6.25 | 34f3d1e4a2927676f669b90f2c157561 |
| .RSRC | 1353135 | 1353216 | 7.05 | 8a57b5e599a3b5f4121f328b42e9fb16 |
Activity Summary
- Drop HWP document in the same directory
- Attempt to open HWP document
- Drop %TEMP%[0-9A-F].dll
- Load dropped DLL
- Invoke EmptySub Method
- Drop C:ProgramDataHncHncChecker.dll
- Create C:ProgramDataHncserial.info
- Create C:ProgramDataHncstatus.dat
- Add New Service
- HKLMSystemCurrentControlSetServicesHncCheck
- Log keystrokes
- Write into C:ProgramDataHncuserdata.cab
Analysis
| A1 | SAMPLE POSSESS ANTI ANALYSIS FEATURES |
| Source: | Static Features, Signature Match, Dynamic Behaviour |
Sample has unusual section names and sections with high entropy, which usually indicates some form of executable packing and/or encryption. Also, we observed that this sample reacts in the presence of tools and environment related to malware analysis. A signature scan and further behavior analysis revealed that this file is protected by a software protection tool called VMProtect.
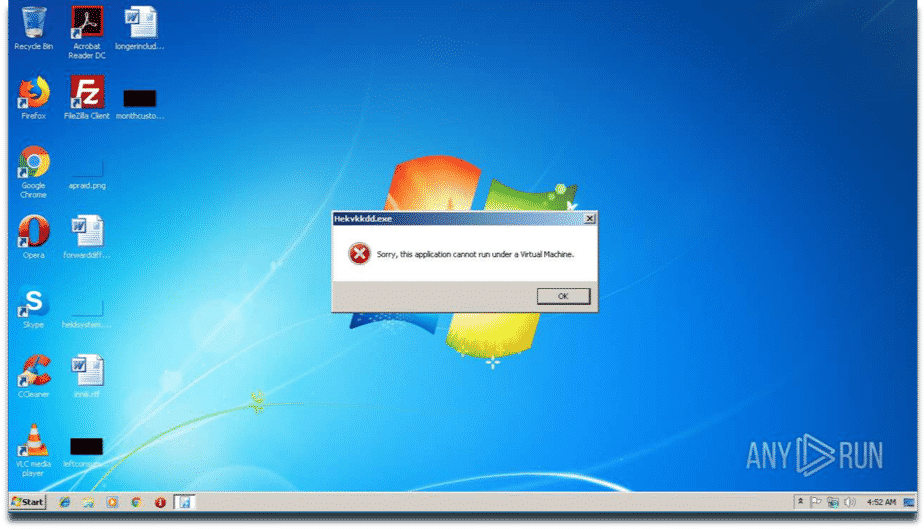
Sample reacting to VM environment
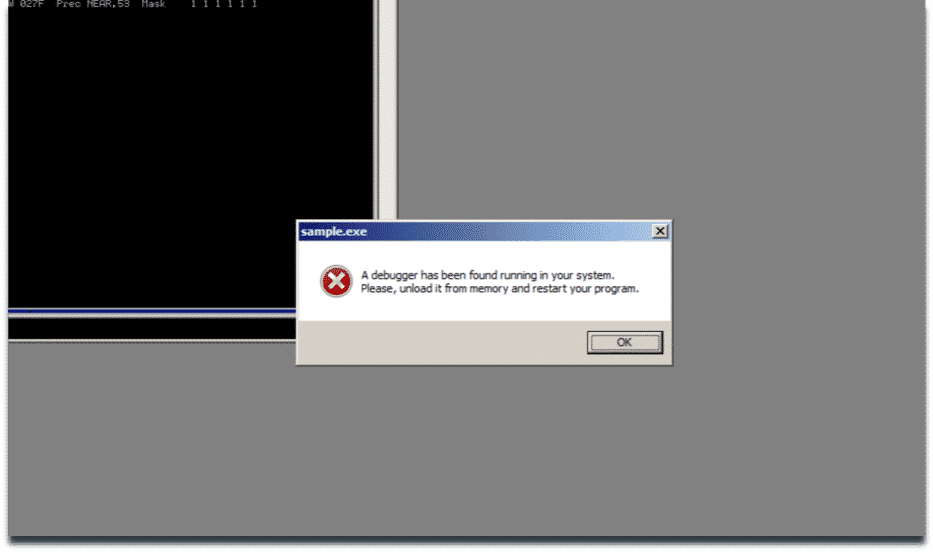
Sample Reacting in Presence of Debugger
- Sample terminates itself when a debugger is attached to it.
- Sample terminates itself in the presence of a process named “Wireshark.exe”
- Sample terminates itself when it detects a Virtual Machine environment.
- Sample employs executable protection and encryption.
| A1 | SAMPLE POSSESS CREATES A NEW SERVICE |
| Source: | Dynamic Behaviour |
It is observed that the sample modifies the system registry in an attempt to add itself as a service and ensure persistence.
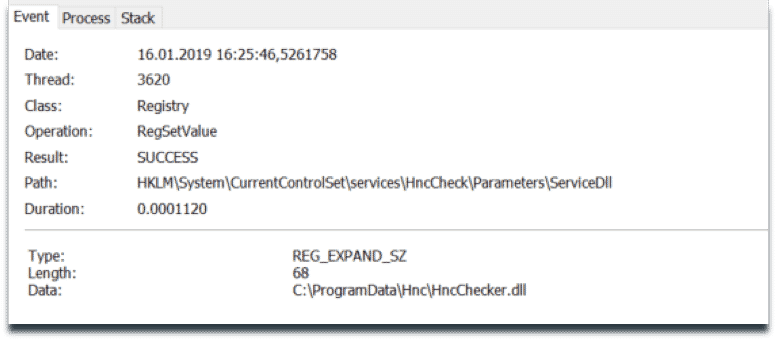
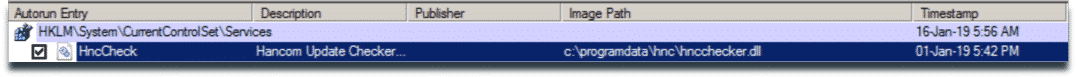
Following registry keys are modified:
- HKLMSOFTWAREMicrosoftWindows NTCurrentVersionSvchostHncCheck
- HKLMSystemCurrentControlSetservicesHncCheckParametersServiceDll
| A1 | SAMPLE DROPS 2ND STAGE MALWARE |
| Source: | Static Features, Dynamic Behaviour |
The sample contains two DLL files in its resources which is assessed to be the second stage payload. Two DLL files are essentially the same payload compiled for different architectures x86 and x86-64. It is observed that malware first determines the architecture of the infected system and then drops the according to DLL file.
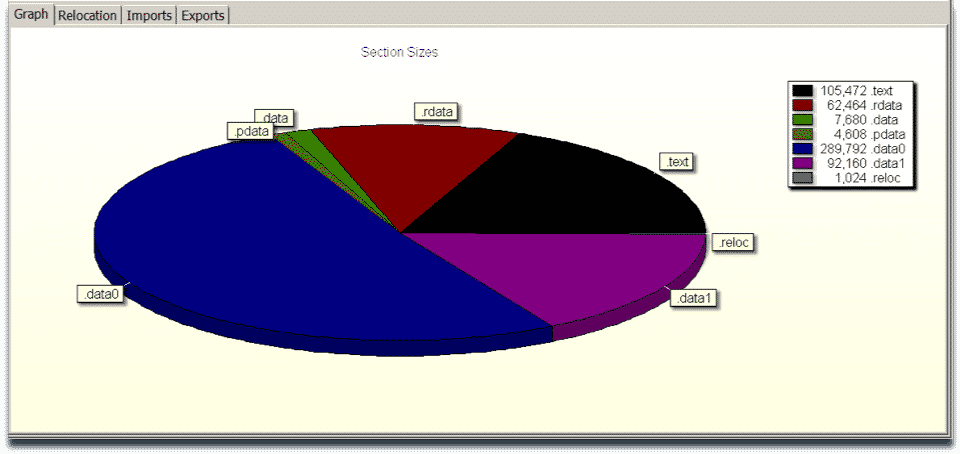
First DLL
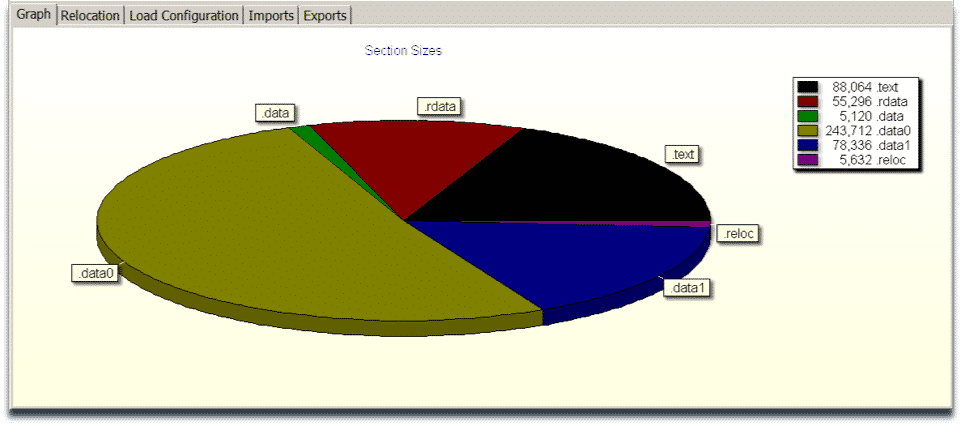
Second DLL
| A1 | SAMPLE IS LOGGING KEYSTROKES |
| Source: | Dynamic Behaviour |
When EmptySub method of dropped HncChecker.dll module is invoked the malware starts to capture keystrokes and writes to local file C:ProgramDataHncuserdata.cab it has created. Although it is not observed we suspect that this malware also contains other collection capabilities.
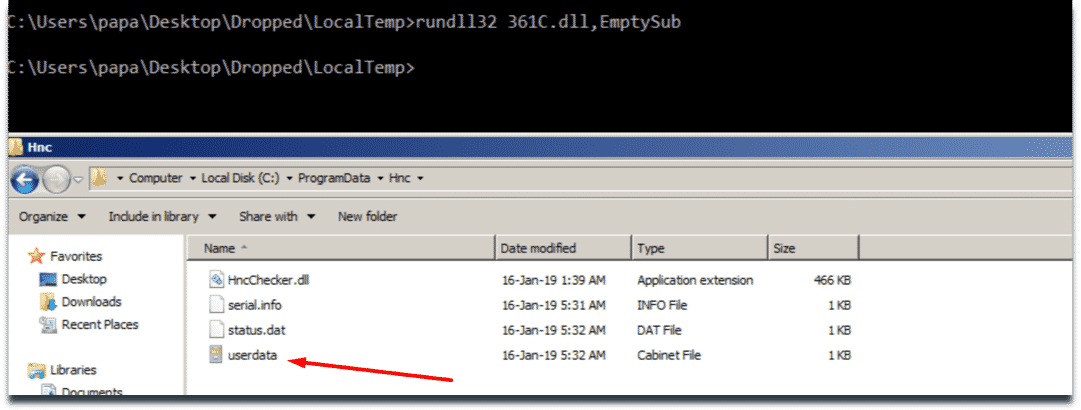
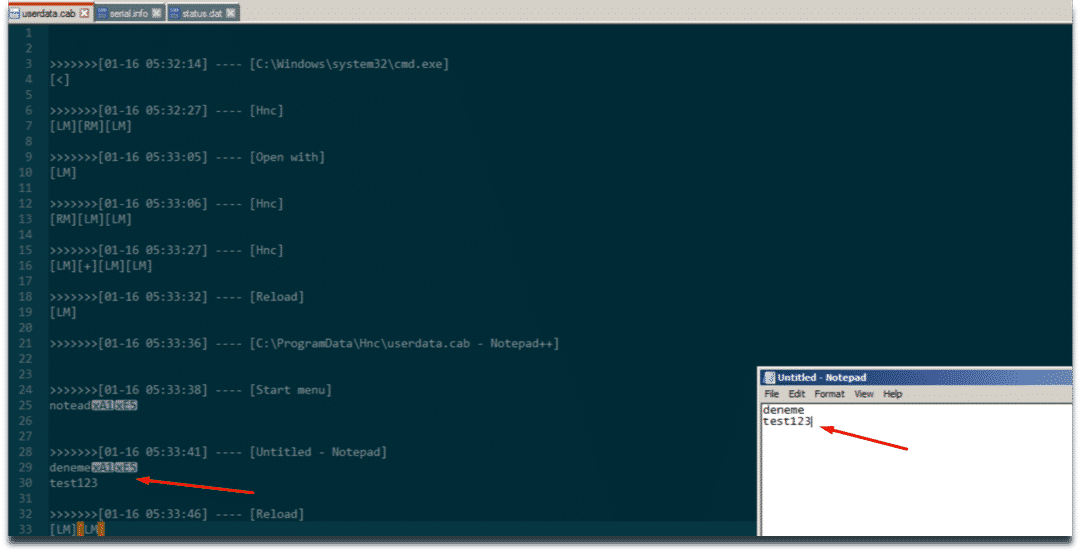
Malware Logging Keystrokes in Local File
| A1 | SAMPLE IS COMMUNICATING THROUGH ONLINE SERVICES |
| Source: | Strings |
We have encountered strings indicating HTTP requests to API of an online E-mail service. This could mean that malware is communicating with its command and control servers through this E-mail service. We also suspect that malware could be using this service for file transfer. However, we have not yet observed this behavior in dynamic analysis environment.

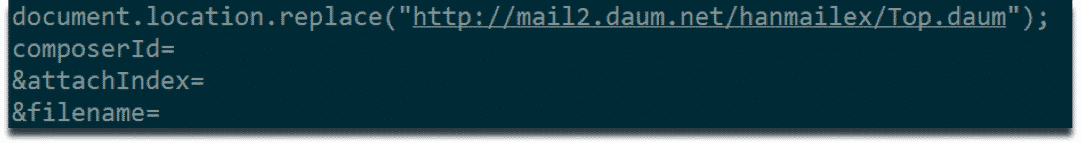
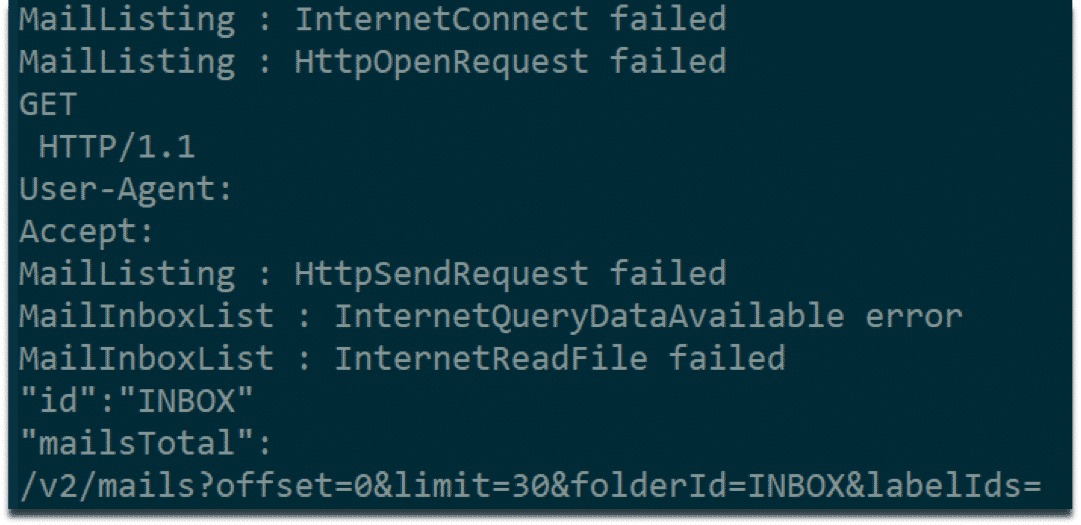
Strings indicating HTTP requests to online e-mail service
| A1 | SAMPLE HAS REMOTE COMMAND EXECUTION CAPABILITIES |
| Source: | Strings |
We have encountered strings indicating remote command execution capabilities. However, we have not yet observed this behavior in dynamic analysis environment.
Cmd [%d] Executing cmd...
| A1 | SAMPLE HAS FILE TRANSFER CAPABILITIES |
| Source: | Strings |
We have encountered strings indicating file transfer capabilities. However, we have not yet observed this behavior in dynamic analysis environment.
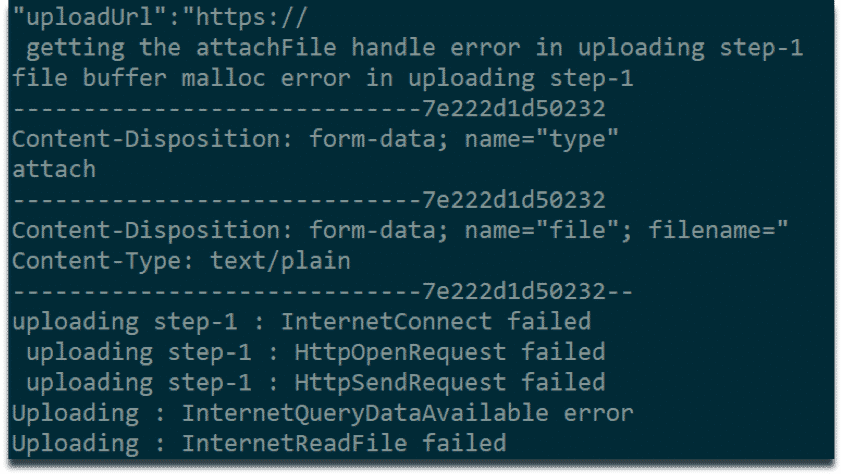
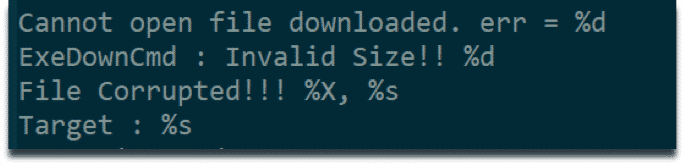
String indicating file transfer capabilities
| A1 | SAMPLE HAS PROCESS INJECTION CAPABILITIES |
| Source: | Strings |
We have encountered strings indicating process injection capabilities. We suspect that this malware can inject any executable into a process, an attacker’s request. However, we have not yet observed this behavior in dynamic analysis environment.
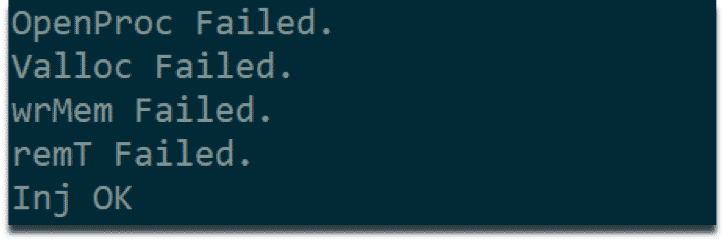
String indicating process injection capabilities
ADVERSARY TACTICS
Several tactics used by this sample is mapped accordingly with MITRE’s Adversarial Tactics, Techniques & Common Knowledge.
| Initial Access | Execution | Persistence | Defense Evasion | Collection | Command and Control |
| Spearphishing Attachment (T1193) | Execution through Module Load (T1129) | New Service (T1050) | Obfuscated Files or Information (T1027) | Input Capture (T1119) | Web Service (T1102) |
| Command-Line Interface (T1059) | Process Injection (T1055) | Automated Collection (T1056) | |||
| Software Packing (T1045) |
Articles from the workshop




